Content Security Policy CSP Reference Examples
OVERVIEW
CONTENT-SECURITY-POLICY.COM RANKINGS
Date Range
Date Range
Date Range
CONTENT-SECURITY-POLICY.COM HISTORY
WEBPAGE PERIOD OF EXISTANCE
LINKS TO WEB SITE
Manipuler quelques conteneurs sur des environnements de développement est une tâche facile. Comment gérer les dysfonctionnements? Comment gérer les déploiements et leurs emplacements? Comment gérer le scaling? Comment gérer les mises à jours? Comment gérer la communication entre les conteneurs? Définit la .
Reputation management and consumer protection for the Bitcoin ecosystem. Establish your reputation and check the credibility of others based on reviews, web-of-trust network and social identity verification. Our chargeback-like process allows a trusted agent to reverse payments and protects users against fraud. Choose a trust agent from our marketplace as an arbiter for your transactions, or offer arbitration services in exchange for fees.
Links will not work in preview mode. 2018-009- Retooling for new infosec jobs, sno0ose, Jay Beale, and mentorship. Do mentorship and apprenticeship in their respective orgs. Best methods to retool yourself if you are.
Reticula, electronica, and oddities. First, the file is loaded as a binary ArrayBuffer.
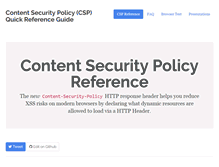
Is a header that allows you, the developer or security engineer, to define where web applications can load content from. Mitigate attacks such as cross-site scripting. If you already love CSP, this site can help you get up and running with it quickly. How To Use This Site. Ready to test out your own policy? .
The command line interface for ambitious web applications. Ember CLI is the Ember. Command line utility that provides a fast Broccoli. Powered asset pipeline, a strong conventional project structure, and a powerful addon system. Which turns ES2015 module syntax.
Email, calendars and contacts done right. Get private, secure, ad-free email hosting for you or your business. Try it free for 30 days. Get 30 days on us, no obligation, no credit card required Try It For Free. Need email hosting for your business? Trusted by 150,000 customers in 150 countries. Depended on by 40,000 businesses every day. Reliably hosting email for more than 15 years. Over 30,000,000 spam emails stopped every day. Stay focused with our beautifully designed, ad-free interface.
Subscribe to our new blog! Saturday, February 21, 2015. Wednesday, January 7, 2015. Bitstamp problem and warm wallets. We are publishing an exciting report on Peatio. Another thing warm wallet should do is ba.
Please help and show your support. Notes taken during day two at CFCamp 2015 in Munich.
WHAT DOES CONTENT-SECURITY-POLICY.COM LOOK LIKE?


CONTACTS
Foundeo Inc.
Peter Freitag
PO Box 8253
Utica, New York, 13505
United States
CONTENT-SECURITY-POLICY.COM HOST
NAME SERVERS
WEBSITE IMAGE

SERVER OS AND ENCODING
I found that content-security-policy.com is weilding the nginx operating system.PAGE TITLE
Content Security Policy CSP Reference ExamplesDESCRIPTION
Content Security Policy Reference Guide and ExamplesCONTENT
This web page states the following, "HTTP response header helps you reduce XSS risks on modern browsers by declaring what dynamic resources are allowed to load via a HTTP Header." We saw that the web site said " Try our CSP Browser Test." It also said " Note It is known that having both. Causes unexpected behaviours on certain versions of browsers."SEEK SIMILAR BUSINESSES
The Art of Data Protection. Discover eSafe Content Security v8.
360 Das studentische Journal für Politik und Gesellschaft. Archiv für Wissenschaft und Praxis der sozialen Arbeit. BIOS Zeitschrift für Biographieforschung, Oral History und Lebensverlaufsanalysen. DDS - Die Deutsche Schule.
Every business is treated for accounting purposes as a separate entity. It is when the goods change hands or when the money is paid. The realization principle of accounting states that we recognise and record the sale when the goods change hand.
Take me home and give it to me. Posted on Saturday, 7 March 2015. Posted on Saturday, 7 March 2015. Posted on Wednesday, 24 December 2014. Posted on Sunday, 9 November 2014. Posted on Sunday, 9 November 2014. Posted on Sunday, 9 November 2014. Posted on Sunday, 9 November 2014. Posted on Sunday, 9 November 2014. Posted on Sunday, 9 November 2014. Posted on Monday, 3 November 2014.
About changing technologies and more. TagSpaces - Your Hackable File Organizer. This free online encyclopedia has achieved what Wikipedia can only dream of - Quartz. By Cybso 7 months ago.